As insurance fraud continues to evolve more aspects of the crime involve digital technology. In the UK, where a considerable amount of policies are generated through online transactions, much can be learned about the customer through the devices used to procure coverage. Device reputation, according to Max Anhoury, vice president of Global Partnerships for iovation, is a way for insurers to do just that.
The 10 year old company focuses on PCs, laptops, mobile phones and tablets that online criminals use to commit their crimes.
“Probably the best example would be…in the UK…if you’re getting an online quote for auto insurance, the insurer would reach out to us in real time and ask us about the device…that computer or that laptop that’s making that online quote,” said Anhoury. “We’ll see whether that device has ever had a bad experience, like first or third party claims fraud. Maybe it’s a good device, but it’s actually related to another device that had a problem at a financial institution somewhere else in the world. Then we’ll take a look at that device for any sort of anomalies. Are they doing things that we think would be risky from that underwriter’s perspective.”
The company doesn’t trace the IP address but rather the actual device.
“What we do is we create a unique global fingerprint for that device. We can identify, and then re recognize that device whenever it comes back to any of the sites that we protect anywhere in the world,” said Anhoury.
The whole process takes a few hundred milliseconds, he said. The device reputation score provided to the insurer can be used to determine policy pricing and to evaluate the integrity of the applicant.
Recently the company was involved in a big bust, a crash for cash scheme centered in the UK. It’s one of the larger schemes Anhoury has seen. The target UK insurer claims identifying and stopping that fraud ring saved it $3.5 million.
According to iovation, crash for cash incidents involve fraudsters either deliberately crashing their own vehicles together in private or braking sharply in front of an innocent driver’s car, causing that driver to rearend them.
“Crash for cash schemes might involve one innocent party and one non innocent party or it might be multiple parties that are all part of the same fraud ring, but in a sense, what they’ve done is they’ve initiated a liability for the insurance carrier by receiving a policy. Then they’re looking to monetize that with a fake accident,” Anhoury said.
In this scheme, four men filed false claims of whiplash. A device was linked to one of the online auto insurance policy purchases. iovation was able to identify additional policies purchased through the device. The insurer used identity records to determine the credit cards used for these purchases and identified other policies purchased with those same cards. Five devices (laptops, a desktop and a mobile phone) were linked with hundreds of policies. The company identified the devices and IP addresses used by the men and the City of London Police located one specific home address where all of the claims originated from.
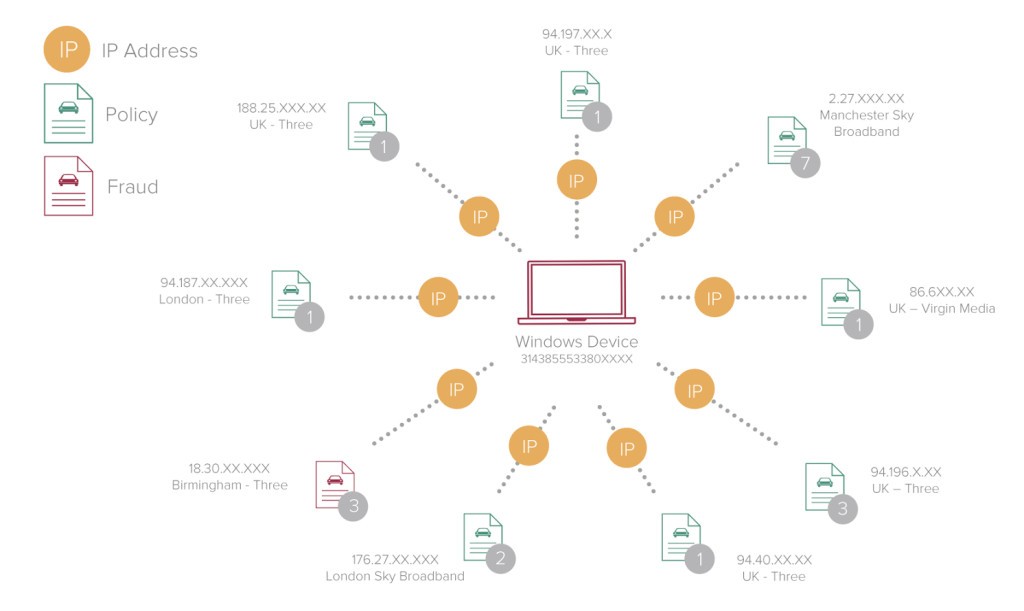 Anhoury said the targeted UK insurer had the ability to associate the name, address, VIN and other information that might be associated with a particular policyholder.
Anhoury said the targeted UK insurer had the ability to associate the name, address, VIN and other information that might be associated with a particular policyholder.
“They’ve got good algorithms to be able to check credit and look and see whether or not there are policies that are related based on that personally identifiable information. For instance, if they had 30 different policies that were issued to a fraud ring and three of those policies shared the same address… their systems could link those together or begin to get a sense that those policies were linked together, even if they were with different people,” said Anhoury.
But fraudsters are learning to hide linkable information as a part of these crash for cash schemes, he said.
“There might be 10, 15, 20 different policies that are all originated by an organized fraud ring. They might not share any common information whatsoever that you could find by examining the details of the policies,” said Anhoury. “We give them an absolutely unique view of those policies because we focus on the device that was used to originate that particular policy. Even though all the credentials might be different, we can tell that the same device was associated with multiple policies.”
The insurer found a couple of common data elements among the suspicious claims by reviewing common attributes like name, address and phone numbers. They also looked at what they could find from a device and IP address perspective.
“Just to be clear, we don’t use IP address as a device identifier, but it was one of the components that they looked at when they were pulling this fraud ring together,” said Anhoury. “They found some that were tied together via a common device. The same device would have originated multiple policies even though they were with completely different insureds.”
“Proxy piercing,” was another tool the company offered the insurer. Often, he said, a criminal will steal an innocent victim’s credentials in order to show an IP address that has a geo location that’s very close to the victim’s location.
“What I don’t want to do is try to initiate a policy for Max Anhoury in Phoenix, Arizona with an IP address that looks like it’s coming from Serbia because that would throw a red flag for anybody doing an online transaction,” he said. “A tool called an anonymous proxy allows me to assume an IP address from any geo location that I like. If I’m a fraudster, I’ve got Max’s stolen credentials in Phoenix, then I’m going to use an anonymous proxy to show up with an IP address that geo locates to Phoenix so I don’t trip a red flag.”
According to Anhoury, the company’s technology can evaluate whether a proxy is in use and also tell where the “IP address actually is, where that computer actually is, regardless of the anonymous proxy that they’re using.”
The insurer utilized the combination of data elements that they had in their system, the combination of device identification and reputation, and proxy piercing technology to hone in on common IP addresses that were associated with the policy originations, he said.
“Because of our ability to pierce that proxy, we were able to isolate some of those IP addresses that were static,” said Anhoury. “A lot of IP addresses, for instance, on the phone systems that you use, you’ll get a different IP address every time you log on or move between different locations. At your house, you might have…what we call a static IP. The IP is fixed – it never changes. It turns out that we were able to locate several of those static IPs. Those were static, so they located to a specific physical address. That’s what allowed us to actually contribute to busting this group of online criminals.”
Besides crash for cash schemes, Anhoury said another growing insurance fraud is ghost brokering.
“Ghost brokering is very, very popular in the UK, and is becoming a real issue for U.S. insurers as well,” Anhoury said.
The fraud typically involves immigrants not familiar with the insurance system.
“They will work with somebody in their community who is known as a ghost broker. This would be someone who would represent themselves as being a broker for Geico, Progressive, Esurance or one of the online providers. They will make the online application for the insured,” said Anhoury. “They likely will misrepresent the actual insured. There will be premium evasion. They’ll tailor the policy to try to get the best rate that they can, even though it’s not commensurate with the risk. They’ll vary address information. In some cases, they’ll actually pay for the policy with stolen payment credentials.”
The victim, he said, may or may not actually have a policy.
“If they do have a policy, it’s not commensurate with their risk so they have problems if they ever do have a claim. You likely have some payment issues there, as well, where the payments will be denied after the fact,” said Anhoury.
According to Anhoury, other types of fraud like policy manipulation and exaggerated or fictitious claims are also seen in the UK.
“The big difference is that the UK insurance market is just fundamentally much more advanced from an online transaction perspective than we are here in the US. The vast majority of policies for home, travel, auto, pet insurance are originated online in the UK,” he said. “They have, over the last 25 years, moved away from a broker model and moved more towards an online model. We see the same types of frauds we just see a lot more of them in the UK, because it’s so much more online.”
Because iovation is a consortium-based model, all the sites that it protects contribute information to the service. As a result, the company can see crossover fraud taking place early on.
“We see a lot of what we call crossover, where we have fraudsters that might be super active on the social sites where they’re gathering personal credentials. They might be then using that to go to annualcreditreport.com and try to pull a credit bureau to get the rest of the information for the victim,” Anhoury explained. “They’ll then take that information and they’ll go to an online credit issuer and they’ll apply for a credit card. They’ll get the credit card, and then they’ll go to an online retailer and they’ll buy a laptop, or whatever it is, handbags, that they want to resell. Then they’ll ship those on the shipping companies.”
Because the company works within a variety of different verticals it can tell that criminals are not focused on any one vertical.
“We often find that the online criminals that are associated with banking fraud, retail fraud or with scamming and spamming in social spaces are the same ones that are active in the insurance space,” he said.
Was this article valuable?
Here are more articles you may enjoy.

 Portugal Rolls Out $2.9 Billion Aid as Deadly Flooding Spreads
Portugal Rolls Out $2.9 Billion Aid as Deadly Flooding Spreads  Hackers Hit Sensitive Targets in 37 Nations in Spying Plot
Hackers Hit Sensitive Targets in 37 Nations in Spying Plot  Founder of Auto Parts Maker Charged With Fraud That Wiped Out Billions
Founder of Auto Parts Maker Charged With Fraud That Wiped Out Billions  UBS Top Executives to Appear at Senate Hearing on Credit Suisse Nazi Accounts
UBS Top Executives to Appear at Senate Hearing on Credit Suisse Nazi Accounts 