

Ransomware attacks became both more frequent and more brutal in 2019, according to a new report by speciality insurer Beazley.
Beazley said its Breach Response Services unit saw a 131 percent increase in ransomware incidents last year. What’s more, a larger share ofransomware attacks with programs such as Ryuk and Sodinokibi were made in tandem with banking trojans such as Trickbot and Emotet, the insurer said in a press release Monday.
“In these cases not only must the affected company deal with the debilitating impact of its critical systems and data being encrypted by the attackers, but the presence of these trojan artifacts often requires an additional assessment of whether data was also accessed or stolen,” Beazley said.
The hackers are also demanding more money. Seven or eight-figure ransom demands are not unusual.
Increasingly, hackers are turning their attention to vendors, perhaps believing that the interconnected relationship would increase the pressure to pay. Beazley said a vendor was targeted in 17% of ransomware attacks.
“These attacks caused business interruption to many downstream customers, ranging from the inability to access data housed in a software application, to a full blown attack on the customer systems as well,” the insurer said.
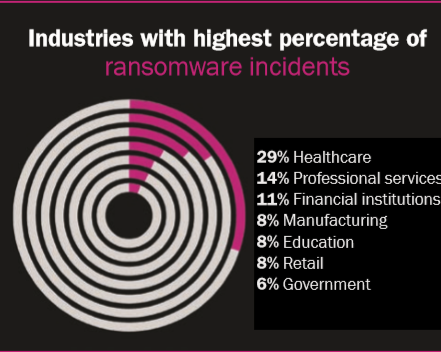
Beazley said the two most common forms of attack to deploy ransomware are phishing emails and breaching poorly secured remote desktop protocol. RDP allows employees to access their work computer desktops or company’s primary server from home with the press of a button, but the convenience also comes with added risks, the insurer said.
“With the convenience of enabling employees to work from home, using RDP can make IT systems more susceptible to attack without the right security measures in place,” saiid Katherine Keefe, Beazley’s head of breach response services. “The coronavirus has forced many more employees to work from home and in this pressured environment it is very important that companies take the right steps to reduce the vulnerability of their IT infrastructure.”
Keefe said its important that employers prohibit remote connections to their networks without multi-factor authentication. Also, employers should create a “whitelist” of e-mail addresses or domain names from which messages can be received. Employers need to make sure that unique credentials for remote access are in place – particularly for third parties.
In 2019 and into 2020, BBR Services recorded an increase in reported attacks by policyholders whose systems were breached via cyber attacks against their IT managed service providers. In some cases these attacks stopped the operations of hundreds of customers downstream from the IT provider, Beazley said.
Keefe said ransomware has developed into a more serious and complex threat over the past four years.
“Although these attacks can be damaging and complex, some of the most effective preventative measures are relatively simple,” Keefe said.
Source: Beazley